
The pandemic vaulted the governments and businesses into the next stage of digital transformation and online services. Everywhere, organisations have been compelled to accelerate and bring forward their digital transformation strategies.
Data is increasingly at the core of any business or organisation and is a critical raw material for intelligent analytics and the driving force behind digital transformation. The widespread move towards remote work and the corresponding need for better remote workforce security has also spurred investment in Zero Trust security. The ability to authenticate and monitor all traffic, regardless of its position inside or outside of an organisation’s network, promises to reduce or eliminate many security risks.
Cyberattacks are constantly evolving and getting more sophisticated, driven by accelerated digital transformation – moving to cloud, rolling out new applications and e-services at lightning speed to address the needs of citizens and customers.
With the pandemic fundamentally changing reality, the question is: How can organisations future proof their infrastructure, keep their data safe and stay resilient?
The 7th Annual Singapore OpenGov Leadership Forum 2022, Day 4, was held on 20 May 2022 at Singapore Marriott Tang Plaza Hotel. It convened digital leaders from the Singapore public sector and financial services industry to discuss, deliberate, share and plan for the next phase of transformation.
Digital transformation as the new imperative

Mohit Sagar, Group Managing Director, and Editor-in-Chief, OpenGov Asia, kicked off the session with his opening address.
We are creating a lot of data, Mohit remarks as he reflects on the metaverse. He pointed out the growing trend of the metaverse, the alternate reality and the billions that are poured into it. “This is where things are going,” Mohit firmly believes.
With the copious amount of data that we need to manage, the security of data is fast becoming imperative. Using racing as an analogy, Mohit revealed that for an F1 race car, about 30% of the cost is spent on the braking system.
“You can only go at high speeds knowing that you can safely and quickly stop. In a digital world, cybersecurity is the brake and safety net,” Mohit claims. “If you don’t know how to protect, you can’t use or democratise data.”
We have been coping the past two years with ‘band-aid’ technology, Mohit feels. These ad hoc solutions and platforms that were used during the pandemic need to be scaled up, taken forward and mainstreamed. Using COVID-19 as an excuse for temporary measures is gone.
Singapore is so connected that it is a prime target for ransomware, Mohit asserts. Accordingly, Singapore jumped to No. 11 globally for ransomware in the first half of 2021. It was 44th in the first six months of 2019 and 21st in the first half of 2020. Two in five SMEs in Singapore suffered a cyber incident over 12 months from September 2020 to 2021.
When thinking about what is happening and the number of hackers that are turning their attention to Singapore, security is no longer something that can be avoided.
The move towards cloud is inevitable, Mohit contends. However, migration is a journey and a process that needs to be safeguarded at all times and every stage. Compared to CEOs, CFOs and COOs, the CISOs of organisations are never sleeping. “The security teams have a tough job,” Mohit acknowledges.
There is a massive paradigm shift in the world and data is rapidly gaining prominence. In this digital landscape, Mohit has an acronym that helps highlight the pillars of transformation and success – ACDC2. ‘A’ stands for augmented intelligence, ‘C ‘stands for convergence (of the physical and virtual), ‘D’ is data, and the last ‘Cs’ stand for cyber resilience and critical events.
The world is changing rapidly, and no one knows what will happen next. As such, Mohit urges delegates to learn from experts who are adept and experienced in keeping data safe and protected.
In conclusion, he encourages delegates to look for partners who are champions in their field of work who can help organisations keep their glass full so that they can focus on their business objectives.
Designing a Single Digital Touchpoint for Businesses
 Simon Ang, Deputy Director – Moments of Life (MOL), Government Technology Agency of Singapore (GovTech) spoke next on GovTech’s journey of developing a single touchpoint across agencies.
Simon Ang, Deputy Director – Moments of Life (MOL), Government Technology Agency of Singapore (GovTech) spoke next on GovTech’s journey of developing a single touchpoint across agencies.
There are a plethora of things that a business owner needs to do including applying for permits and licences. What government agencies can do is ease the process so they can be spent on business development activities.
Simon shares that the main problem business owners were beset with was the prolonged amount of time required before their licenses are all approved. Most F&B business owners would find a location and will pay a deposit to secure the venue, only to spend 3-6 months afterwards applying for licences. In addition, many were not completely aware of the sequence of applications.
Tasked with the mission to streamline this process, GovTech started to understand its users. Accordingly, they: 1) Engaged 41 different F&B businesses and spoke to the owners and administrative staff 2) understood the pain points in every agency touchpoint 3) Sought views on how the license application process can be an integral part of their business process
Undertaking a service journey approach, they used the service blueprinting technique to map the user’s journey across the different agencies during their application. They grouped agencies that are in parallel processing and lay them in a sequential flow.
Instead of making the user go through the different agencies on their own, business owners would provide all the information at the start and their application will be routed automatically from one agency to the next – users will simply receive notifications when their applications advance.
The new system integrates 11 systems, which are linked through 17 APIs and enables people to get their application in 2 weeks.
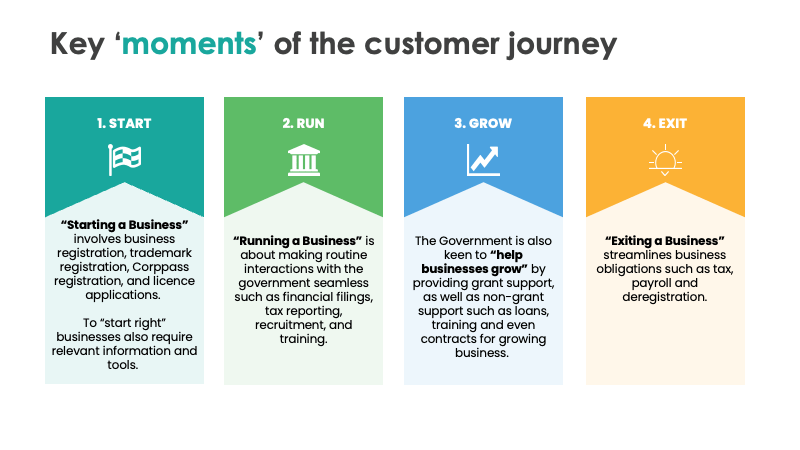
GovTech’s role is to look at different sectors and industries, as well as the key moments when users are interacting with the government. Through the pandemic, GovTech adapted to the needs of users and continued to develop applications that can help lubricate processes.
In conclusion, Simon believes that technology is there to help organisations stay relevant and to improve the quality of service.
Innovation and Modernisation in the Public Sector

Vishal Ghariwala, Chief Technology Officer, APJ and Greater China, SUSE spoke next on the trends of digital transformation through cloud-native technologies.
Vishal observes that the government’s budgets point to 3 priorities in digital transformation: 1) Meeting citizen expectations – modern and always-on services 2) Adapting to threat vectors and 3) Sustaining Resilience amidst uncertainty
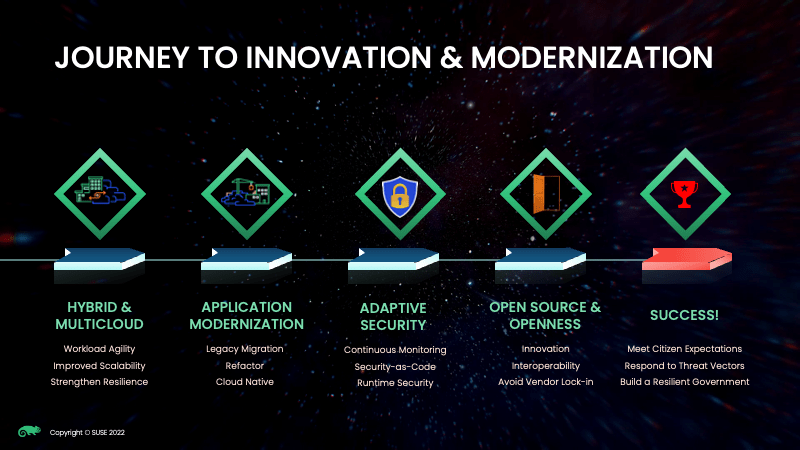
Cloud migration is a journey that will continuously evolve, Vishal contends.
First, it begins with setting up a multi-cloud platform. With the fabric in place, application modernisation is the next stage. Thereafter, it is followed by adaptive security. Vishal concurs that threats are evolving rapidly, which is why technologies in security need to be updated consistently. He adds that automation needs to be looked at to streamline processes.
Vishal believes that open-source technologies provide a firm foundation for innovation and openness is the ability to interoperate with other vendors.
SUSE Rancher enables organisations to take the best of what a hybrid cloud can offer. “SUSE is committed to co-creating success,” Vishal states.
NeuVector addresses many issues of security and, because the technology is open-source, it can be used with the existing technologies of organisations.
Vishal shares a case example of an agency that needed a flexible cloud platform primarily used for data analytics in disaster detection and prevention. The organisation wanted it to be agile, scalable and able to support modern containerisation, all while being affordable and providing the highest performance. Unfortunately, affordability and high performance usually do not go hand in hand – which is why they looked to open-source solutions.
Building an entirely new, cloud-native technology needed the following:
- Scalable and flexible = easily and automatically scalable across different regions based on traffic surges and peaks. Infrastructure must be built quickly to respond to emergencies
- Affordable and high performance
- Multi-tenant
- Container-based architecture
- Built using Open-Source technologies
- Support mobile and remote workforces and field operations
In response to the needs of the organisation, SUSE came up with a solution with the following features:
- 7-Region national scale AI (Artificial Intelligence) cloud platform (2 Private cloud, 5 Edge cloud)
- Each cloud region is a full OpenStack environment – Software defined provisioning of GPU and NVMe resources
- Core-to-Edge architecture supports both local and mobile/remote workforces
- Workloads are containerised and orchestrated using Kubernetes and SUSE Rancher Container Management Platform SUSE Rancher orchestrates via the OpenStack plugin to create a secure multi-tenant environment
- Built using open-source technologies: SUSE Rancher, Kubernetes, OpenStack
Eventually, they were able to deliver the following benefits for the customer:
- Regional COVID symptoms and test results can now be aggregated across two core environments
- AI/ML models to detect COVID hot spots
- Implement regional restrictions
- Inform mass population around COVID hot spots
- Easy and transparent access to COVID-related information
SUSE Rancher Benefits
- Quickly adapt and scale the system
- Automated orchestration and provisioning of workloads
- Zero-touch deployments
- Ease of administering distributed infrastructure
Vishal assured delegates that SUSE can support organisations in their transformation journey, to enable organisations to deliver impact to their users or customers. He encourages delegates to reach out to him if they are keen to find out how SUSE will be able to add value to their services.
The key to building a resilient digital infrastructure

Kamal Naresh: The key to digital resilience is next-gen data management
Today’s Information Technology environments are beset with new challenges, Kamal contends. Issues are aplenty – increase in threat vectors due to the massive amount of remote work, increasing regulatory oversight dictating rules for privacy and retention and legacy infrastructure limitations that prevent companies from being more agile.
Almost all companies are leveraging the cloud in some capacity and many have mandates to embrace it in bigger capacities, but it is not that easy. Additionally, IT is being held to stringent SLAs and many stakeholders have zero tolerance for downtime.
Backups are often considered the last line of defence. To put that in a football context, there is an entire line (or two) of defenders that try to prevent the opponent from ever scoring. The goalkeeper acts as that last defender that saves the ball from going into the goal. Not only do goalkeepers prevent others from scoring, but they are also the ones that put the ball back in play.
What Cohesity does is very similar, Kamal explains. Not only does Cohesity protect the goal and prevent data from being lost, but they are also the company that restores it to the environment. Ransomware has evolved and is now attacking backup copies. As a result, there is a need for a different architecture.
At its core, Threat Defense is about providing customers with a highly resilient platform that ensures confidentiality, availability and integrity of the data with encryption, fault tolerance and immutability built into the platform.
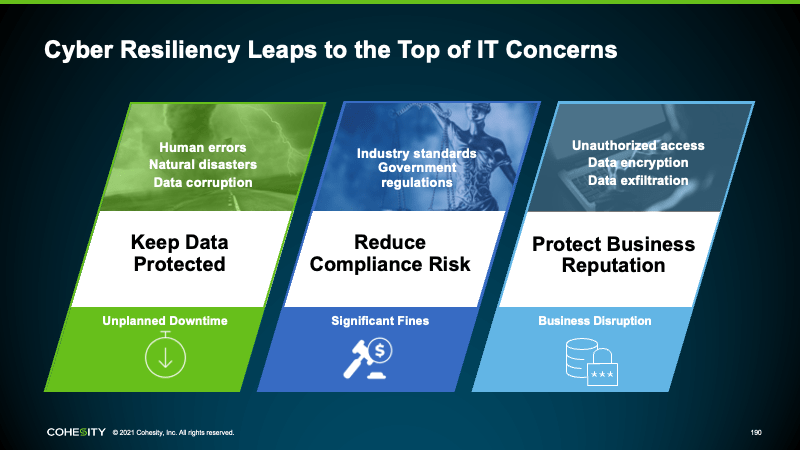
Data resiliency is then further augmented with comprehensive access control capabilities that ensure that entities accessing the data management platform conform with Zero Trust principles of no implicit trust and authentication, authorisation, and access control at the UI, CLI, and API-based entry points.
Kamal explains that it is further strengthened with support for multi-factor authentication, granular and customisable role-based access control to enforce the principle of least privilege and segregation of duties and quorum-approval to prevent unitary over privilege within administrative accounts – a crucial control to protect against unintentional user error, rogue admins, or compromised accounts – as well as auditing and continuous monitoring capabilities to ensure compliance and operational integrity of the entire data management platform.
However, unique to Cohesity, the Threat Defense architecture incorporates additional layers of protection: AI-driven detection and analytics – a set of advanced capabilities ranging from data classification to near-realtime threat detection to source-side data anomaly detection to adaptive behavioural analytics.
These detection and analytics capabilities provide Cohesity customers with the knowledge of where their sensitive data resides to proactively address compliance and governance issues like data overexposure in a near-real-time manner before these threat actors manage to fully exfiltrate an organisation’s most sensitive data assets.
The final layer of Cohesity Threat Defense ensures that their data management platform can be securely operationalised by their customers. This layer ensures that Cohesity remains an open and extensible data management platform with capabilities like our Marketplace that allow leading security ISVs like SentinelOne and Tenable to build security apps that run close to the data to help protect the data, natively on the Cohesity platform.
He concludes that data is always dark in the recovery phase, which makes automation necessary to identify what is violating compliance policies. Cohesity offers organisations to do bulk recovery and integration for security operations. Cohesity Threat Defense architecture can help to keep data secure as part of an overall in-depth defence strategy.
Polling results for the morning session
Throughout the morning session, delegates were polled on different topics.
The first poll inquired about key business initiatives for the next 12-18 months. Almost a quarter (24%) are focused on improving agility and delivery through Cloud Migration. That is followed by efforts to improve employee productivity through digital technology (21%) and modernising and securing apps (17%). Other delegates were evenly split between enabling real-time performance visibility and analysis (14%) and allowing users to efficiently deploy IT services across a variety of environments (14%) while the rest (10%) are embedding compliance transparently in applications.
 Delegates were then asked about what would have the bulk of their budget allocation in 2022 –2023. Delegates were equally divided between improving integrity and governance while reducing inefficiency (23%) and fortifying cyber resilience (23%). While 18% opted for enhancing or adopting AI and Analytics for improving outcomes through forecasting, prediction and optimisation (18%), Similarly, another set of respondents were split between digitalisation of processes to deliver better or ‘Smart’ services (14%) and embracing cloud technology, be it public or private (14%). The remaining selected leveraging IoT (Internet of Things) to improve processes and productivity (9%).
Delegates were then asked about what would have the bulk of their budget allocation in 2022 –2023. Delegates were equally divided between improving integrity and governance while reducing inefficiency (23%) and fortifying cyber resilience (23%). While 18% opted for enhancing or adopting AI and Analytics for improving outcomes through forecasting, prediction and optimisation (18%), Similarly, another set of respondents were split between digitalisation of processes to deliver better or ‘Smart’ services (14%) and embracing cloud technology, be it public or private (14%). The remaining selected leveraging IoT (Internet of Things) to improve processes and productivity (9%).
On the main motivator that is driving digital transformation, most (42%) are interested to improve their capability to manage the increasing amount of data at the edge locations while ensuring security and compliance while 32% hope to speed up their time-to-market to fully capitalise on business opportunities or to serve citizens better. The rest (26%) see a growing need to maximise value/insights from an increasing amount of data assets as a motivator.
Regarding key fears in moving to cloud, a sizeable majority (61%) were concerned about security and governance. The other delegates were split between operational costs (16%), the need to re-skill talent (13%) and vendor lock-in (10%).
The subsequent poll asked delegates what they saw as the biggest challenge in digitalisation and cloud migration. About 42% found people and skillset the biggest challenge and 32% opted for security and compliance risks (32%). Data classification/data sovereignty/data residency concern was an issue for 11%. The remaining delegates were equally split on legacy infrastructure (5%), executive support/top management strategy (5%) and budget (5%) challenging.
Inquiring about the cyber security concerns that organisations are most worried about, 42% were worried about phishing and spear-phishing campaigns. The rest of the delegates were evenly divided between attacks on public-facing websites and infrastructure,e.g., SQLi, XSS, DDOS, (21%) and social engineering campaigns targeting employees/partners/users (21%). The rest of the delegates are bothered about attacks on remote access infrastructure, e.g., VPN compromise (17%).
On their plans to implement Zero Trust across their extended environment, most (43%) have already started implementing zero trust with a primary focus on identifying our critical assets, while others (29%) are partnering with multiple security partners to build a practical and pragmatic roadmap to implement zero trust. The remaining delegates have made huge investments in different technologies and are not sure where to start due to operational complexities (21%) or are not yet ready to implement zero-trust due to a lack of resources and skills needed (7%).
Asked about key drivers for their organisation’s initiating/augmenting an identity access/Zero Trust management programme, over a third (35%) identified Security/Data Protection/Breach Prevention to be critical. It was followed identically by operational efficiency (18%) and addressing hybrid IT security issues (18%). Similarly, another set equally indicated reducing endpoint, Insider and IoT security threats (12%) and internal/Industry/Regulatory compliance (12%). The rest of the delegates are driven by the response to audit or security incidents (6%).
On the external help needed most to accelerate their digital transformation journey, about a third (35%) want assistance in managing the complexities of monitoring and managing multiple tools on on-premises and hybrid multi-cloud-based systems. That is followed by the mindset change and new ways of working (26%), agile Integration (17%), training and enablement for cloud technologies (13%) and automation (9%).
Exposing Supply Chain Attacks in Modern App Development

Tan LyeHee, Director of Sales Engineering, APAC Middle East & Africa, Checkmarx, elaborated on cyber threats in modern app deployment.
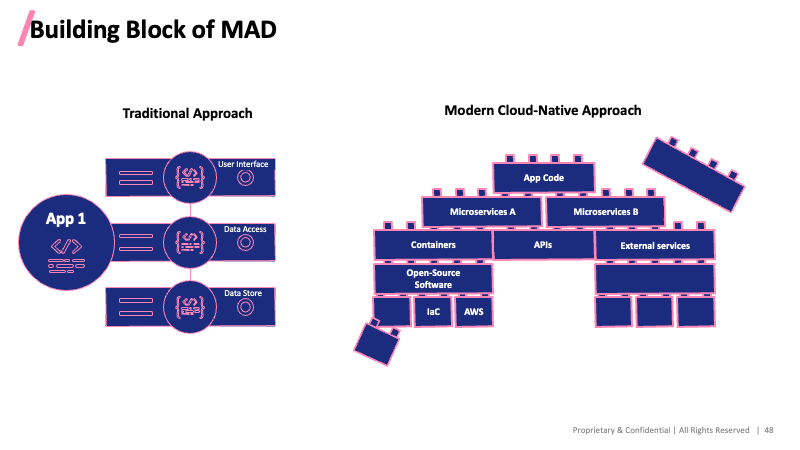
LyHee began by addressing the question of what Modern Application Development (MAD) is. MAD is a new approach to creating and increasing value through software produced. It holds the key to modernisation and software-based digital transformation. Through it, rapid innovation is powered using cloud-native architecture, loosely coupled microservices, database and service modules and it can abstract from the underlying system. It can dynamically respond to events in near real-time and offers tremendous benefit
However, MAD brings new security “risks” such as container risks, infrastructure as code risks, API (Application Programming Interfaces) Risks, Open-source code risks and Microservices Risks. Checkmarx takes the approach of modules and engines stacked on the cloud. It has been a pioneer for software security for years and is now transforming the industry to move beyond traditional security testing to managing the total software exposure across their entire SDLC at the speed of DevOps and the business.
More than 1,400 of the world’s leading organisations trust Checkmarx to power their software security program. They are a leader in the 2018 Gartner Magic Quadrant and are ranked #1 by industry peers on Gartner Peer Insights. Its proven solutions implemented by their customers have led to some phenomenal growth, we are growing 70% year-over-year and now have close to 600 employees globally.
The greatest challenge is supply chain security, opines LyHee. Checkmarx began with open-source software where codes are copied in modules from other places. The open-source module comes from other modules.
LyeHee observes that collaboration across wide communities has driven an explosion in application development based on open-source software. Highly collaborative ecosystems have myriad advantages, but zero trust security controls are not one of them, and attackers are taking advantage.
Accordingly, he shares the anatomy of an attack:
- A good package goes bad
- Discovery of other common packages being infected
- Attackers go after the developers preparing the package
- Minor and major versions were infected
Considering the prevailing trends, LyeHee believes that software composition analysis is the focus. There is also a need to understand the organisation’s open-source risk profile:
- Accurate open-source library detection
- Risk dashboard and detailed reporting across the organisation
- New vulnerability alerting without the need to rescan
- Vulnerability trends over time (project-level)
- Leverage the comprehensive threat intelligence database of public (CVE) vulnerabilities and unique (Checkmarx research)
In conclusion, LyeHee believes that mitigating against supply chain attacks is an imperative that should not be ignored. Through triage scan results they can identify and visualise the dependency structure, as well as dig into transitive elements. They are also able to focus and know where the vulnerable library is from before understanding the component to remediate.
He urged delegates to reach out to Checkmarx to better understand how the technology can help their organisations.
Observability in Singapore’s digital transformation journey

Taylor Chan, Head of Sales Engineering, Asia Pacific, SolarWinds talked about observability in digital transformation.
Taylor considers Singapore to be one of the fastest adopters of digital technologies. It is a mature market and an early adopter of new technologies, applications and solutions. The nation is forging ahead with its vision to have a world-class, secure and resilient 5G infrastructure that will be the backbone of its digital economy.
Singapore is a magnet for visionaries and businesses looking for an innovation hub in the Asia Pacific. A growing pool of highly skilled talent, solid government support schemes and an advanced IT infrastructure make up the triumvirate behind Singapore’s global competitiveness.
In addition to serving as the region’s trading centre, Singapore is universally regarded as the #1 Tech hub in the Indo-Pacific, a key reason 4,500+ U.S. companies are in the country. It has built a world-class, globally competitive tech industry and continues to explore new frontiers in innovation such as cloud computing, artificial intelligence, quantum computing, data analytics and other technologies that span healthcare, security, fintech, energy, aviation and defence.
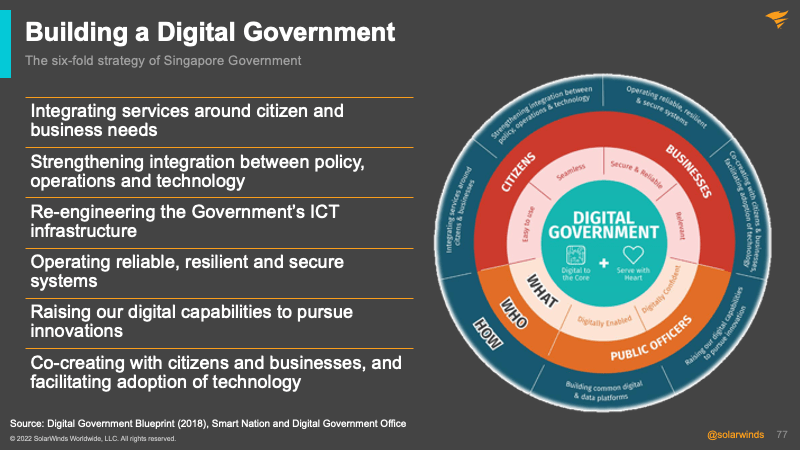
The borrowing cost for Singapore is significantly less as it has historically maintained a high credit rating of AAA. For Taylor, Singapore is doing tremendously well in digital transformation and employs a six-fold strategy.
Some of the best examples of the Singapore government’s services include:
- SingPass: Digital identity for easy and secure access to government and private sector services
- MyInfo: Digitalisation of business operations via API which has resulted in an 80% improvement in application time
- LifeSG: One-stop access to 70+ government services for different stages of life
- GoBusiness: Connect business owners to 300+ government services, which teaches people how to apply for licenses.
For Taylor, there are some key features of a digital government:
- Services that are easy to use, reliable and relevant
- Seamless digital transactions
- Systems and data that are secure
- A digitally confident public service workforce
- A digitally enabled public service workplace
Those features have enabled swift actions to be taken to support COVID-19 operations:
- TraceTogther, SafeEntry; Build on existing tools like SingPass, MyInfo, FormSG
- Allow rapid development within days – Maskgowhere (Within 36 hours) and SupplyAlly
The foundations allow the government to quickly build applications. A prime example is Maskgowhere, which was ready within 36 hours, including a system that tracked the mask collection progress across 743 collection centres. This allowed resources to be directed to centres where help was needed.
The COVID-19 pandemic produced an urgent need to address logistical challenges on a national scale. For example, the distribution of reusable face masks to all Singapore residents created a logistical challenge to track collection quotas and manage a flexible pool of volunteers. SupplyAlly – A mobile app developed by GovTech to facilitate nationwide logistic distributions.
The beauty of the system is that the underlying technology is hidden from the citizen. It is an elegantly engineered product which provides a secure way to connect the different Government services. The good part is that the complexity of services faded into the background, and the citizens can enjoy the benefits introduced by the systems.
Taylor points out that Core Operations, Development Environment and eXchange (CODEX) technology stack enables them to use less sensitive data outside of their infrastructure, such as commercial cloud.
The Singapore Government Technology Stack (SGTS) comes with four aspects:
- Digital services: Easy to use, accessible and secure digital government services that improve the lives of citizens and businesses.
- Microservices: Reusable common services that agencies utilise to build applications such as the National Digital Identify for authentication.
- Middleware: Software services such as APEX (API gateway) and WOGAA (Whole of Government Application Analytics) (analytics that allows for rapid development, deployment, testing, and monitoring)
- Hosting platforms: Scalable hosting containers with secure connectivity.
Hence, GovTech has created a centralised government-wide API exchange -APEX – that serves as a searchable library of APIs. Authentication protocols on APEX ensure that only authorised applications have access to highly confidential citizen data. At the same time, activities on the APEX platform are tractable as the system audits and logs the applications that have requested to pull data from government databases.
With APEX, data collected and stored by one agency can be used by numerous other approved agencies or businesses to improve and streamline their processes. For example, MyInfo leverages the capabilities of APEX to enable citizens and residents to manage the use of their personal data for a myriad of online transactions, including applying for a Housing Development Board flat and opening a bank account.
The MyInfo API for developers makes it possible for more applications to be integrated with MyInfo without significant hassle or overhead costs.
To Taylor, the goal of digital transformation in government organisations is easy-to-use, secure services for citizens, and seamless digital transactions between people, government and agencies.
- Adopt new business models, operating models, and platforms: Go Digital First and Leverage data-driven insights into the services
- Avoid outdated processes and disruption causing mechanisms: Adopt automation (RPA) and modernise legacy systems
- Implement digital practices instead of physical counters: Leverage self-service digital practices
- Leverage newer technology and Analytics: Make use of forecasting and predictive modelling
- Invest in emerging technologies: Aim for a scalable and secure digital platform
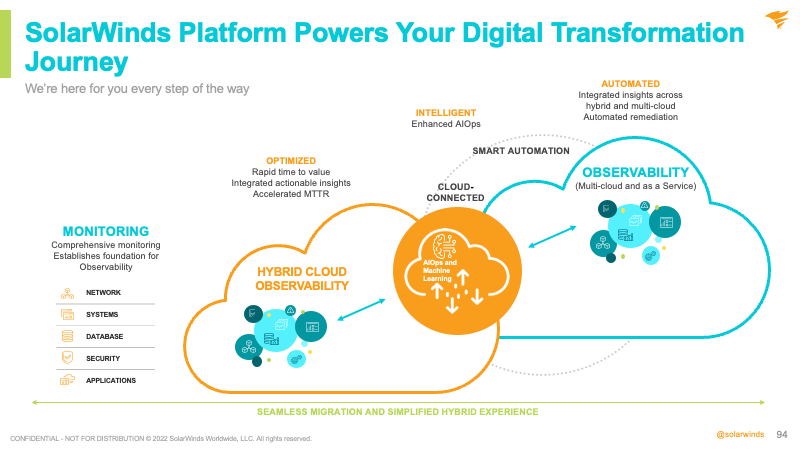
Digital transformation spending is set to explode, Taylor believes that the areas of need include the revival from the pandemic, cost and productivity, and growth and results. Getting there will require faster decisions, simplified work, and the elimination of needless tasks. Considering that, full-stack visibility has never been so critical, Taylor contends.
Where SolarWinds can help is in proactive monitoring. With different tools and technology being adopted by companies the IT teams are left with spending most of their time dealing with performance issues. When organisations have too many tools, it can cause slow root-cause analysis. This leads to downtime, added cost and operational inefficiencies.
In conclusion, Taylor shares that the SolarWinds platform can support and power the digital transformation journeys of organisations, delivering superior ROI in various industries. He encourages delegates to reach out to his team to find out more about how SolarWinds can help with their organisation’s journey.
Mitigating digital asset disruption in a time of flux

Nathan Stevens, Head of Solution Consulting – APAC, Snow Software, shared on the complex and evolving space of digital asset disruption and how it can be addressed it.
“We are in a continuous state of disruption,” Nathan observes. “What we consider a digital asset has changed dramatically, and the emergence of new asset classes has made managing them even more challenging.”
He believes that IT leaders must leverage technology that delivers comprehensive visibility and contextual insight – Technology Intelligence. It allows for the management of organisations’ complete technology landscape and to drive transformation with precision and agility.
Digital assets have significantly changed in the last 40-50 years, but that rate of change has been exponential with the emergence of new technologies.
What is seen in this disruption is an increase in complexity. Buying practices have changed, and the world is very much in a consumption economy, and moving into a per second per minute economy as well – transforming into business-led procurement. Cyber-security exposure is larger than ever and very much high on the radar for all CIOs, especially as attacks become common. Identifications of vulnerabilities and foreign agents launching new attack has everyone on all on high alert.
The utility in which we associate these digital assets has expanded greatly – everything from ensuring your plants have enough water, to full automation of a mining site with driverless trucks – the possibilities are endless
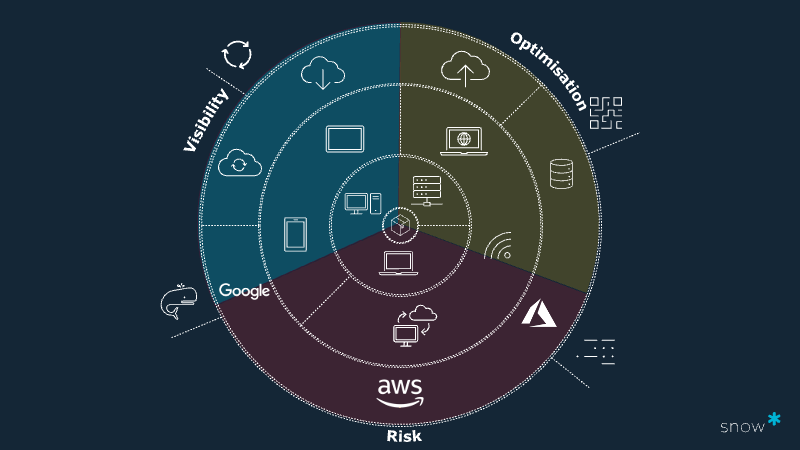
Looking at how the modern digital asset was formed, Nathan wants to assess each of these distinct ages of modern technology against the spectrums of visibility, optimisation potential, and risk.
- Visibility – achieve a holistic view of data, applications, and spending across on-premises data centre, cloud, and SaaS (Software as a Service) environments
- Optimisation – leverage intelligent insights and recommendations about your data to optimise spending and drive operational efficiencies
- Governance – manage security risk and compliance without affecting business performance
All this points to common themes for 2022 and beyond, namely the rise of IoT, 5G, AI/Machine Learning, RPA, low code applications and edge computing and, more recently the meta-verse. All are rapidly changing how people consume technology and how we approach data and IT operations.
Nathan points out that cyberattacks on IoT devices skyrocketed in 2018 and surpassed 300% in 2019. Accordingly, malware attacks are now affecting a vast number of IoT devices. According to Forbes, the number of malware incidents involving IoT devices has grown from 813 million in 2018 to a staggering 2.9 billion already the following year.
The results of not having adequate visibility in place are:
- Lack of optimisation and increased risk
- Increase in SaaS spend that we are locked into and grown comfortable then, then the price increase
- Huge uptake in new technologies that need to be managed and will have huge impacts I.e., Containers
- 85% of CMDB projects fail – trying to achieve too much or being too ambitious; completeness for completeness’s sake or trying to achieve 100% coverage in a dynamic and ever-changing environment
“We don’t need a single source of truth, we need to have different data sets that give us a different perspective or insight – and integrate those best of breed datasets into the CMDB only where it makes sense,” Nathan asserts.
Snow’s solution for Technology Intelligence – what we see as the future of Software Asset Management is to provide complete insight and manageability across all technology
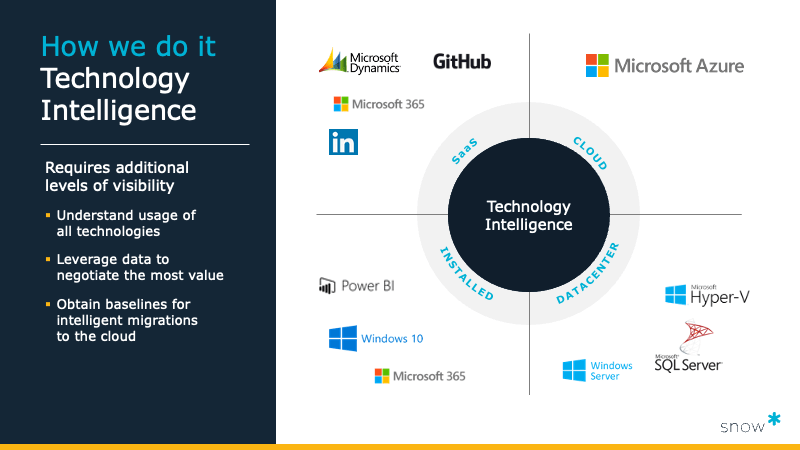
For Snow Software, the approach to technology intelligence requires additional levels of visibility, which involves understanding the usage of all technologies, leveraging data to negotiate the most value and obtaining baselines for intelligent migrations to the cloud.
If managing Microsoft spending as one key use case, it is possible to apply the same logic to Oracle or VMware as well. There is a movement beyond software or hardware asset management – it is time for technology asset management.
In conclusion, Snow Software can help organisations provide intelligence on the data that is collected to make business decisions on that data. The platform allows them to bring real value to customers. Nathan adds that they are also able to integrate with business processes.
Polling results for the afternoon session
Throughout the afternoon session, delegates were polled on different topics.
The first poll inquired about key business initiatives for the next 12-18 months. Over a third (37%) were focused on improving agility and delivery through Cloud Migration. This is followed by efforts to modernise and secure apps (21%) and enable real-time performance visibility and analysis (21%) and improve employee productivity through digital technology (11%). The rest were focused on allowing users to efficiently deploy IT services across a variety of environments (5%) and embedding compliance transparently in applications (5%).
Delegates were then asked about what would have the bulk of their budget in 2022 –2023. Just under a third (32%) have committed to embracing cloud technology, be it public or private (32%), followed by the digitalisation of processes to deliver better or ‘Smart’ services (26%). The remaining delegates have their allocation for n enhancing or adopting AI and Analytics for improving outcomes through forecasting, prediction and optimisation (16%), fortifying cyber resilience (16%) or improving integrity and governance whilst reducing inefficiency (11%).
On the main motivator that is driving digital transformation, 39% are driven by the desire to speed up their time-to-market to fully capitalise on business opportunities or to serve citizens better, followed by the growing need to maximise value/insights from an increasing amount of data assets as a motivator (26%). The rest of the delegates opted for providing a consistent and seamless cloud-everywhere experience across a distributed organisation (22%) and improving their capability to manage the increasing amount of data at the edge locations while ensuring security and compliance (13%).
 Regarding key fears in moving to cloud, well over half (58%) were concerned about security and governance. The other delegates were split between the need to re-skill talent (25%), operational costs (8%), and vendor lock-in (8%).
Regarding key fears in moving to cloud, well over half (58%) were concerned about security and governance. The other delegates were split between the need to re-skill talent (25%), operational costs (8%), and vendor lock-in (8%).
The subsequent poll asked delegates what they saw as the biggest challenge in digitalisation and cloud migration. Delegates were evenly split between people and skillset (21%), legacy infrastructure (21%) and executive support/top management strategy (21%). The rest of the delegates equally found security and compliance risks (14%), budget (14%) and data classification/data sovereignty/data residency concerns (7%) challenging.
Inquiring about the cyber security concerns that organisations are most worried about, most delegates (42%) were worried about phishing and spear-phishing campaigns. The rest of the delegates were split between attacks on public-facing websites and infrastructure, e.g., SQLi, XSS, DDOS (21%) and social engineering campaigns targeting employees/partners/users (21%). The rest of the delegates are concerned about attacks on remote access infrastructure, e.g., VPN compromise (17%).
On their plans to implement Zero Trust across their extended environment, delegates are evenly split between partnering with multiple security partners to build a practical and pragmatic roadmap to implement zero-trust (28%), having made huge investments in different technologies and not sure where to start due to operational complexities (28%). Others (17%) have already started implementing zero trust with a primary focus on identifying their critical assets while about 7% are not ready to implement zero-trust due to a lack of resources and skills needed.
Asked about key drivers for their organisation’s initiating/augmenting an identity access/Zero Trust management programme, over a third (35%) identified Security/Data Protection/Breach Prevention to be essential. It was followed by internal/Industry/Regulatory compliance (36%) and addressing hybrid IT security issues (14%), The rest of the delegates are driven by the response to audit or security incidents (7%).
On the external help needed most to accelerate their digital transformation journey, most (42%) need assistance with a mindset change and new ways of working, followed by managing the complexities of monitoring and managing multiple tools on on-premises and hybrid multi-cloud-based systems (26%), training and enablement for cloud technologies (21%), automation (5%) and agile integration (5%).
Closing
To conclude the day, Mohit stresses the importance of getting started on the journey of securing data and information because “data is the new oil.”
For Mohit, attacks are inevitable, and organisations need to ramp up security to continue delivering business outcomes and value. He believes that the key is to work with partners who have the expertise and knowledge so that energies can be channelled into driving business objectives.
















