Critical services and manufacturing companies must be aware of the evolution of cybersecurity and understand the threats that exist today and may emerge in the near future. This will enhance the safety of systems, protect intellectual property, and key data. Robust safeguards for critical services offer tangible protection against massive losses and build consumer confidence in the services provided by the system
Ideally, these protections should be incorporated in the design of a new system. Where it is not practical or cost-effective to replace legacy systems, additional enhancements may be warranted to strengthen protection against current and emerging threats.
Critical services and manufacturing have risen from the eighth to the second most targeted industry by cyber attackers, trailing only finance and insurance. This represents a 300% increase in a single year, according to the 2021 Global Threat Intelligence Report (GTIR).
In one example, Colonial Pipeline, the United States’ largest pipeline system for refined oil products, paid a reported US$ 5 million ransom to hackers in 2021 after an attack on its IT (Information Technology) network had forced it to shut down its entire pipeline, causing major disruptions to gas delivery.
An estimated 62% of Malaysian organisations have detected an increase in cyber data breaches during a workplace shift, with 25% or more alerts on cyber threats since the pandemic began. In July 2021, the Malaysian Employers Federation was hit by a ransomware attack involving encrypted accounting data. Its servers were down for three days. Months later, a hacker targeted a Penang-based web hosting company, disrupting its virtual private server and Windows hosting services, demanding US$ 900,000 in cryptocurrency as ransom.
Ransomware does far more than merely infect and corrupt files and devices. When ransomware gains access to a device or database, typically by masquerading as a suspicious file or link, it encrypts critical data and makes it inaccessible to anyone who does not have the correct key. The hacker will demand an exorbitant ransom for the key and failure to pay within the time limit usually results in the data being destroyed or made public.
This can have disastrous consequences, such as a serious breach for critical services and manufacturing organisations, where operations will be halted, and trade secrets will be exposed, resulting in a significant loss. Moreover, clients’ personal and private data, including banking details, physical and electronic contact details may then be exploited by the hackers and their criminal associates to directly target clients.
Accelerating the deployment of security tools with dual defence strategies to ensure reliable backup and recovery will ensure that common cyber threats will not significantly disrupt the critical services and manufacturing supply chain. An effective backup strategy is currently considered the best line of defence against ransomware attacks.
As the risk of ransomware and related attacks increases, the additional effort and investment required to protect an IT system become increasingly justified; it is no longer a ‘nice-to-have’ but is likely to become a mandated requirement for critical infrastructure.
The OpenGovLive! Virtual Breakfast Insight on 24 March 2022 aimed to provide insights and practical solutions that enable critical services and manufacturing organisations to maximise their data capability through comprehensive, centralised and efficient data protection and more cost-effective and secure data-driven processes.
Staying secure in a rapidly changing world

Kicking off the session, Mohit explains how rapidly the world has changed, “We do not need a bullet to cripple the economy.”
Cybersecurity-based attacks are all it takes to acquire data and infiltrate organisations. For Mohit, the playing field is not level because the bad actors are evolving their techniques quickly and intelligently – they are persistent and relentless, driven by profit (or ideological) motives and not bound by rules or geography.
Organisations need to look at not only fortifying their infrastructure but their whole supply chain infrastructure. “Security is how organisations can keep their lights on.”
“You will get hit. Everyone will get hit,” Mohit believes. “The question is, what is your recovery strategy what is your backup plan?”
With remote working in the picture, employees have become the weakest links and point of entry for attacks. From a Singapore perspective, Mohit asserts, the number of hits has multiplied.
Closing his address, he urges delegates to partner with the experts instead of doing everything in-house. “Let the experts help to keep your glass full,” Mohit encourages. “It not only allows the best systems and infrastructure to be put in place but also frees up the organisation’s staff to concentrate on the business and focus on driving growth.”
Approaches to security in the manufacturing industry

Rajiv Arora, Global Head of IT Global Hub, Siemens spoke next on the strategies and approaches that can be taken in organisations.
“Now is the time to implement security. Do it now and do it right,” Rajiv opens.
He observes that the ground has shifted and there are more considerations in the cybersecurity landscape:
- Changing geopolitical context
- A more complex and connected supply chain
- Changing customer needs are changing
- Maintaining a competitive advantage
- Intensifying revenue
- Lack of human talent and resource
Rajiv shared five pillars to digital transformation:
- Decipher the ambition: Ambitions need to be driven by optimisation and transformation
- Structure the transformation: There is a need to set up a proper structure for cybersecurity and backup
- Co-Create the roadmap: Work with your team to co-create the baseline of the roadmap
- Execute and control the implementation: Organisations need to be aware of the weakest link in every transformation and ensure that cybersecurity is an integral part of the implementation
- Incubate and ramp up the operation: After having the baseline, organisations will then be able to look at scaling the operations.
As for the digital transformation approach, Rajiv shared the 4E Model:
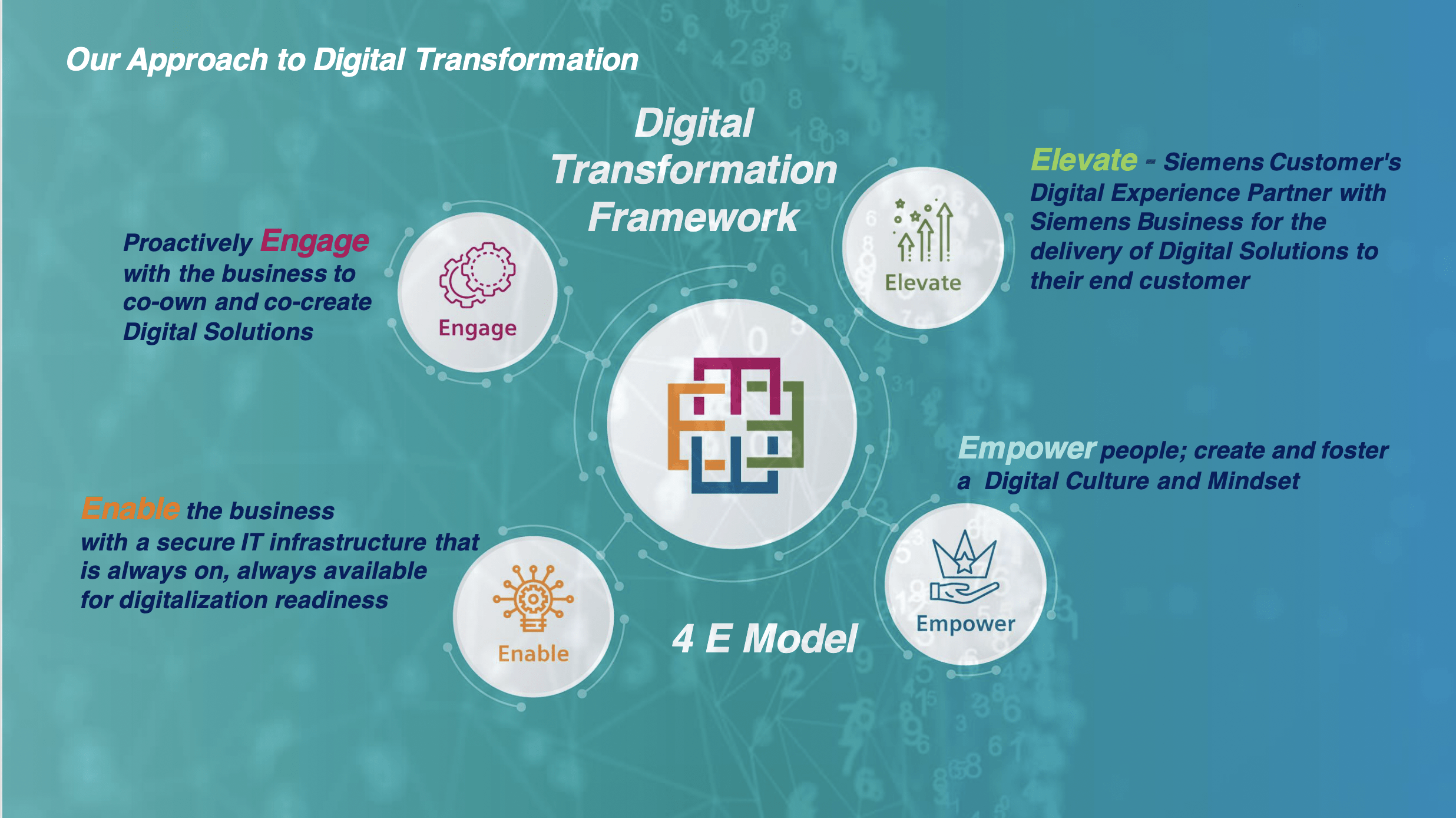
- Engage – Proactively engage with the business to co-own and co-create digital solutions
- Idea sourcing: collecting ideas for improvements in processes that deliver business benefits using IT enhancements or radically new Digital Solutions
- Communities: Communities are set up and engaged using a formal approach to generate new ideas, prioritise demands, upgrade and keep solutions sustainable.
- Campaigns: To encourage a change of mindset and adopt new ways of making.
- Elevate – Elevating the customer’s digital experience and partner with businesses for Digital Solutions and support the development of new business models
- Innovation: Leverage Emerging Technologies to innovate and enhance business model, develop, and expand Digital portfolio.
- Business Impact: Collaborate with business in prioritising, commercialising, and executing the digital solutions/products and creating Business Impact -Value for customers.
- Enterprise Governance: An enterprise governance model that promotes transparency and exchange of digitalisation outcomes between the Siemens business and IT; Metrics and KPIs to evaluate business outcomes.
- Enable – A secure infrastructure that is always on, always available and everywhere, as the backbone to ensuring readiness for Digitalisation
- Monitor: “Run IT.” Monitor IT to ensure services are readily available by consistent monitoring Business-As-Usual (BAU) KPIs.
- Optimise: Provide an agile Infrastructure, by optimisation of services with available technologies.
- Modernise: Transform into a modern IT infrastructure by leveraging on a diversity of options in technologies, partners, and solutions.
- Empower – Create and foster a Digital Culture and Mindset using a knowledge-based ecosystem
- Digi Training: Digi Training to address learning needs of employees, leaders
- Digital Champions: Digi Champions to evangelise digitalisation topics in the organisation
- Info Pool: Info Pool of digital technologies and partners –Success Stories and Use Cases
- Agile: Agile and Design Thinking as the new way of working for employees and leaders
Having imparted practical tips towards approaching digital transformation, Rajiv shared his belief that in Industry 4.0, there is a need for organisations to be on a cloud platform. It can help to enhance operations and ensure more secure backups. Security is paramount, Rajiv says, and organisations need to prepare themselves for the imminent and inevitable attack.
Fireside chat
In the next session Mohit engaged in an in-depth conversation with Goh Chee Hoh, Managing Director, Malaysia & Nascent Countries, Trend Micro and Tay Chia Chia, Country Director – Malaysia, Brunei & Emerging Countries, Veeam. Mohit invited the guests to share their opinions on the outlook of digital transformation from their perspective.

Chee Hoh believes that COVID-19 accelerated digital transformation and that some specific trends have emerged.
- Increase in remote users – tore down the security control to the user
- Different priorities between OT and IT
- SaaS (Software as a Service) and cloud will overtake on-prem solutions
Chia Chia, on the other hand, observes that there are two levels of manufacturing in Malaysia – the MNCs and the locally-driven mid-tier to big firms. She observes that while manufacturing companies have the luxury to put proper plans in place – a complete framework for recovery and cybersecurity –local manufacturing companies, however, must devise their strategy from scratch. Apart from that, moving workloads to the cloud is another observable trend.
Mohit feels that when the pandemic first broke out, organisations were quick to adopt band-aid technology, but now that the dust has settled, it is time to look into the security and infrastructure.
When asked about considerations that industry leaders, Chee Hoh believes that there are several key aspects that organisations need to consider:
- Legacy systems leading to security vulnerability
- Lack of priority in applying patches. Hackers can capitalise on these vulnerabilities and attack through the supply chain where organisations are giving access.
- Vulnerabilities from working from home
- Cloud and zero-trust
Chee Hoh acknowledges that cloud offers the agility and speed, but at the same time, security needs to keep up. That said, he agrees that the journey to cloud is inevitable and organisations must ensure that their infrastructure can support it.

Chia Chia stresses the need to build a framework for recovery. In the past people could afford a reactive approach, concentrating on the ability to restore. That is, however, no longer enough for the needs of the present – organisations must adopt a proactive mindset. Smaller organisations without the luxury of proper frameworks need to look for expertise to co-build their framework.
In the current scenario, “back up is the insurance,” Mohit asserts.
Chee Hoh agrees that threats are on the rise and evolving and that there is a need to back up. He differentiates between the traditional and modern threats of ransomware
Traditional: One-attack to many but less destructive
Modern: Targeted, research-based and intended to create multiple damages.
From experience, he knows that there is no silver bullet when it comes to security; organisations need to invest in solutions that anticipate breaches. “You will be hit and you need to reduce impact.”
In terms of practical advice, Chia Chia highlights that strategy can change, which is why organisations must select cybersecurity and backup solutions that are scalable and allow change from time to time.
Veeam can offer protection across all platforms (on-prem, single or multi-cloud). In the closing remarks, she emphasises that Veeam is not limited by the technology that organisations choose.
Power Talk
Looking to explore the rapidly emerging threat of ransomware, Mohit debated the strategies to combat ransomware with the following panellists:

Dr Tan Puay Siew, Division Director, Manufacturing, System Division SIMTech, A*STAR, Myat Min, Section Manager, Manufacturing, Control Tower SIMTech, A*STAR, Sage Khor, Pre-Sales Manager, Malaysia, Trend Micro and Tay Teck Sze, System Engineering Manager, SEAK, Veeam
Sage points out that as people improved on their security and data protection strategy, threat actors are also improving. Echoing Chee Hoh’s earlier point about modern ransomware having launched more targeted attacks, he opines that it is now about identifying the techniques and tactics that threat actors are launching.
To mitigate that, Teck Sze suggests planning out a framework and preventing threat attacks by securing the backup infrastructure and assets. He notes that ransomware has evolved – instead of going to the assets, they attack the last line of defence – the backup data.
Mohit remarks that organisations need to know what their SOPs are like when faced with an attack.
Agreeing, Dr Tan highlights the importance of segregating the corporate network from the IoT (Internet of things) network to secure corporate data. Apart from that, she also recommends securing hardware.
Myat Min added to the list of practical tips by suggesting restricting access from IT and OT and putting in place a firewall. He echoed an earlier point that human errors in the production line are areas of vulnerability.
To mitigate modern-day attacks, Sage urges delegates to invest in security platforms with complete visibility of IT and OT, as well as the attack surface.
Mohit asserts that security is not an option but an investment. Organisations will be hit, and the attention needs to be on disaster recovery.

Teck Sze concurs with Mohit and agrees that this is an area that organisations need to pay enough attention to. He shares that many of his customers are moving towards a hybrid model and are leveraging cloud for disaster recovery. He suggests looking for partners who have the capability to cover disaster recovery.
From her observations, Dr Tan notes that the most vulnerable groups are SMEs. Many SMEs in Singapore do not have dedicated IT teams and outsource such services to vendors, including backups. For these SMEs, there are vulnerabilities in securing their OT environment, and with partners, they can achieve some level of security.
For Teck Sze, cyber recovery is something that everyone in the organisation needs to be familiar with. Only with a full understanding of the recovery process can data recovery be executed.
In terms of protection, Sage emphasised the importance of multi-factor authentication. “Most attacks start with credential issues,” Sage opines. “Apart from that, it is imperative that organisations continuously maintain IT hygiene and patch management.”
Next, he suggests uncovering shadow IT surface and any unused credentials that can be used for attacks. Finally, he asserts that employees are the weakest links and that organisations need to build up the awareness of employees.
In closing, Mohit re-emphasises the necessity of security. It is not an expense or an option but a non-negotiable. Protection is what will enable organisations to drive at full speed and emerge unscathed from any potential crashes.
Interactive Discussions
After the informative presentations, delegates participated in interactive discussions facilitated by polling questions. This activity is designed to provide live-audience interaction, promote engagement, hear real-life experiences, and facilitate discussions that impart professional learning and development for participants.

In the first poll, delegates were asked about the cybersecurity framework that their organisation had or plan to adopt. Almost two-thirds (63%) use The International Standards Organisation (ISO) frameworks ISO/IEC 27001 and 27002. Other delegates use The Center of Internet Security Critical Security Controls (CIS) (11%) or the US National Institute of Standards and Technology (NIST) Framework (5%). The remainder (21%) use other standards.
It is common that people, Sage points out, will have multiple standards that they adhere to because practising the framework is not easy. At the end of the day, it is a point of reference.
Mohit concurred and highlighted that these frameworks offer a base and starting point for organisations to approach security.
The next question asked the delegates their thoughts on whether organisations can implement the same IT Security Strategy into Operational Technology (OT) environment. An overwhelming majority (83%) believe that it needs a different security approach. The remaining delegates were either not sure (11%) or of the view that organisations can just plug and play (6%)
Chee Hoh stressed that the technology needs to fit the environment, which means that a different implementation is required. Teck Sze added that there are differences in the IT and OT environment – IT environment deals with structured data protection, whereas OT deals with unstructured data protection.
Sage acknowledges that while it is difficult to patch on the OT environment, organisations need to develop a virtual patching strategy for IT and OT environments. He suggests doing segmentation of the OT environment and Veeam will be able to assist in controlling the command.
Inquiring about delegates’ first concern for security operations for their organisation, half (50%) were concerned with a cyber security skills shortage. The others found it difficult to determine an actual attack from the noise (25%), advance & zero-day attacks (13%), automate response (6%) and actionable threat intelligence (6%)

Mohit remarks that the world is seeing shortages in data scientists and security experts, to which Rajiv concurred. He added that people working in the cybersecurity space need to learn and adapt quickly because it is always changing.
Sage pointed out that automation in the field of security is a big topic. The crucial question to ask is where automation is applied. For him, automation on detection is necessary for organisations to have complete visibility. Automation in response, however, depends on the environment and priorities, which requires a proper playbook.
The next poll was to determine if delegates have a Security Information and Event Management (SIEM) solution in place. Most of the delegates (43%) are either currently in the plan or have a SIEM solution. The remaining delegates do not have a solution in place (19%).
Chee Hoh asserts that collecting data is important but being able to act on it and have good event management is even more important. “The weakest link is the human,” he believes. “Having the right information of what and where the weak links are important.”
On that note, Dr Tan advises people to secure the end devices of users. Mohit adds that the Bring Your Own Device norm has become a point of vulnerability. Teck Sze reiterated the importance of training employees to be knowledgeable about security and bad habits.
In the next poll, delegates were asked how they manage CRITICAL software vulnerability for both IT and Operational Technology (OT). Over a third (38%) either close all possible attack surfaces or rely on their existing security solutions to prevent the attack (33%). The rest of the delegates patch it immediately (19%) or take other action (10%).
In response to the results, Chee Hoh notes that every organisation faces about 20 vulnerabilities each day, making it difficult to patch. Instead, he suggests virtual shielding in front of the vulnerability, an added layer to protect the vulnerability rather than patch it.
Teck Sze echoed Chee Hoh’s view that vulnerabilities abound. He pointed out that resources to fix vulnerabilities also depend on risk factors – vendors are usually there to fix the higher risk vulnerabilities.
In the final poll, delegates were asked to rate the level of readiness of their organisation to a ransomware attack. An overwhelming majority (95%) feel well prepared but are not sure if their organisation can withstand an infiltration. The remaining 5% feel well-prepared and believe that there is no room for infiltration.
Chee Hoh is of the view that no one can be totally prepared because new malware is created every day. “It is ever-evolving,” he claims. “Visibility is important because that allows people to assess areas that are compromised.”
Rajiv agreed that we are prepared but not for tomorrow.
At the end of the day, Dr Tan opines, “Organisations can only prepare as much as they can, and as much as they know – it’s not possible to know what is enough!”
Chee Hoh suggests organising drills for employees to test their responses and customise courses from there. Apart from that, he also emphasised the criticality of education for the board of directors so that the higher management is aware of security needs.
Conclusion
Mohit thanked everyone, including the speakers and participants, for their enthusiastic participation in the session. He wholeheartedly agrees with Chee Hoh’s point about changing the culture and mindsets of higher management. Mohit encouraged delegates to take their management on the journey of understanding security without them knowing it.
Now is the time to work on securing your organisations, Mohit believes. Organisations must get started immediately, and not only when their organisation is hit.
In closing, he encouraged delegates to reach out to the experts and the partners should they have queries about how they can get started on this journey.