“Singapore has moved from preventing cyber threats to assuming breaches have occurred”, said Josephine Teo, Minister for Communications and Information, Singapore. When Minister Josephine Teo made this statement in Estonia during the Tallinn Digital Summit, she underscored the need to have a strong cybersecurity posture. Singaporeans have not forgotten the cyberattack in 2018, where a quarter of the city-state’s population healthcare records were breached during a cyberattack against the country’s healthcare system.
It was after the 2018 data breach that Singapore’s position on cybersecurity changed from one of trying to prevent attacks to one that assumes that an attack has already occurred. “It’s just a question of ‘when’, it’s not a question of ‘if’,” explained Minister Teo.
Without a doubt, the pandemic has drastically and unexpectedly accelerated the need for a new network security model. Zero trust security is not a new concept, but it has now taken centre stage and security leaders agree that it will improve security and simplify security processes for distributed teams and hybrid networks.
A widespread move to remote work and the corresponding need for better remote workforce security has spurred investment in zero-trust security. The ability to authenticate and monitor all traffic, regardless of its position inside or outside of an organisation’s network, promises to reduce or eliminate many security risks. However, rolling the model out has proven to be complicated, presenting organisations with a mixed bag of successes and obstacles. One key reason is that zero trust adoption is a logistical challenge, not just a technical one. Security modernisation often depends on the progress of user identity consolidation and cloud transformation, both complex and long-term projects.
Moreover, organisations are facing challenges with overall cloud transformation. Organisations have accelerated their cloud adoption plans but are not fully prepared. When large chunks of data have not yet moved to the cloud from isolated data centres, it can become harder to secure using a single security tool. Identity and access management (IAM) complexities also proved equally challenging for zero trust adoption. Teams are struggling to shift to a zero-trust approach due to the complexities of user access needs in their organisation.
Zero trust relies on a single source of truth for identity management, yet larger organisations, in particular, have often accumulated multiple incompatible identity providers over the years. They must also understand access patterns across a huge number of applications — most of which cannot be shut down even for a moment to be migrated to a new identity platform.
The pandemic has further exposed the weaknesses of the traditional ‘castle-and-moat’ security model. Remote work has expanded attack surfaces infinitely outwards – more than ever, agencies need to start from the assumption that their ‘castle’ is already compromised. Zero Trust has emerged as a compelling security framework to address the failures of existing perimeter-based security approaches.
This leads to fundamental questions: what does it take to adopt and deploy zero trust architecture? Are organisations equipped to enhance the efficiency and security of their mission-critical applications and websites?
This was the focus of OpenGovLive! Virtual Breakfast Insight on 1 December 2021, which aimed to impart knowledge on how to deploy the zero-trust model seamlessly and to overcome common obstacles in zero-trust adoption.
Embracing the security imperative in a hybrid world

Mohit Sagar, Group Managing Director and Editor-in-Chief, OpenGov Asia, kicked off the session with his opening address.
COVID-19 has fundamentally changed culture, Mohit asserts. With remote working entrenched in the new normal, hybrid work is the new reality. For him, the world cannot and will not go back to what it used to be – to demand employees return to physical work in offices in the name of security will not bode well.
Organisations must learn how to keep individual secure where he or she is working while keeping the work environment secure. “Culture has shifted and we must evolve with it,” Mohit is firm.
Singapore is embracing a Zero Trust strategy. According to the Singapore Cybersecurity Strategy 2021, the three strategic pillars are: building resilient infrastructure, enabling safer cyberspace and enhancing international cyber cooperation.
Mohit observes that the prevailing priorities of the public sector are to roll out innovative and secured digital services quickly, encourage inter-agency collaboration, enable a hybrid workforce and increase availability and security.
There is no doubt that rapid digitalisation increases the risk that organisations will face. In May 2021, Asia Pacific experienced a 168% YoY increase in cyber-attacks. There were reported malicious attacks that destroyed data in destructive/wiper-style attacks (average cost of $4.52 million) and ransomware attacks ($4.44 million).
“But just because it is a little bit hard, it does not mean that organisations should go back in time and revert to the old model,” Mohit says. Instead, he stresses, organisations need to embrace the challenges of security head-on instead of eschewing them. There is no turning back when it comes to digitalisation. Organisations can no longer hide behind the word “security” as an excuse not to modernise.
Although the challenges of the future abound, Mohit remains optimistic because of partnerships that can enable organisations to expand their capacities. He urges delegates to partner with organisations with a wealth of expertise and experience that can make the journey of security far easier to manage and navigate.
Hedging against cyber-attacks with Zero Trust

Fernando Serto, Chief Technologist and Evangelist, Asia Pacific, Japan and China, Cloudflare spoke on the ways Cloudflare can support agencies in building a secure Zero Trust architecture.
Cloudflare is a global network located in 250 cities in more than 100 countries, one of the fastest, that is trusted by millions of web properties. With direct connections to nearly every service provider and cloud provider, the Cloudflare network can reach 95% of the world’s population within 50 milliseconds.
As a company, Cloudflare provides Zero Trust Services, Cloudflare Network Services and Cloudflare Application Services. With the Zero Trust Services, Cloudflare helps to secure internal operations on a single global network by providing ZTNA with private routing, remote browser isolation, SWG with CASB and identity/endpoint integration.
Most people know Cloudflare for their application services such as WAF with API protection, rate limiting, load balancing, bot management, L7 DDoS protection, CDN and DNS. However, Fernando explains that Cloudflare also offers an integrated global edge platform and harnesses its unified software stack to run all its services. With the network services, Cloudflare offers WAN-as-a-Service, Firewall-as-a-service, L3 & L4 DDoS protection, network interconnection, and smart routing.
On the topic of Zero Trust Services, Fernando explains that the key concept is that it assumes that the network has been breached or that a breach is inevitable. Zero Trust is centred on requiring continuous verification through real-time information. Organisations need to identify and be able to decouple users from the network.
Yet the challenges are aplenty, Fernando warns delegates. He observes that today’s corporate WAN architecture is broken. Perimeter security is a bottleneck and does not work, applications are in the cloud and have a high latency for remote users. It is also difficult to scale and expensive. If anything, Fernando opines, “COVID-19 has taught us that the old model does not work.”
The security perimeter is and will be, constantly susceptible to vulnerabilities. Pulse Connect Secure VPN software has reportedly been exploited by attackers and many are targeted by accident. He adds that applications inside the WAN are also at risk, citing numerous reports of cyberattacks and system breaches. Vulnerabilities will always exist, but, how quickly organisations patch them will make the difference. Regardless, patching vulnerabilities takes time.
For Fernando, the switch to Zero Trust network access with private routing can help to mitigate these issues. With Cloudflare’s offering, security and connectivity are optimised, driving agencies’ speed and security in a work-from-anywhere world.
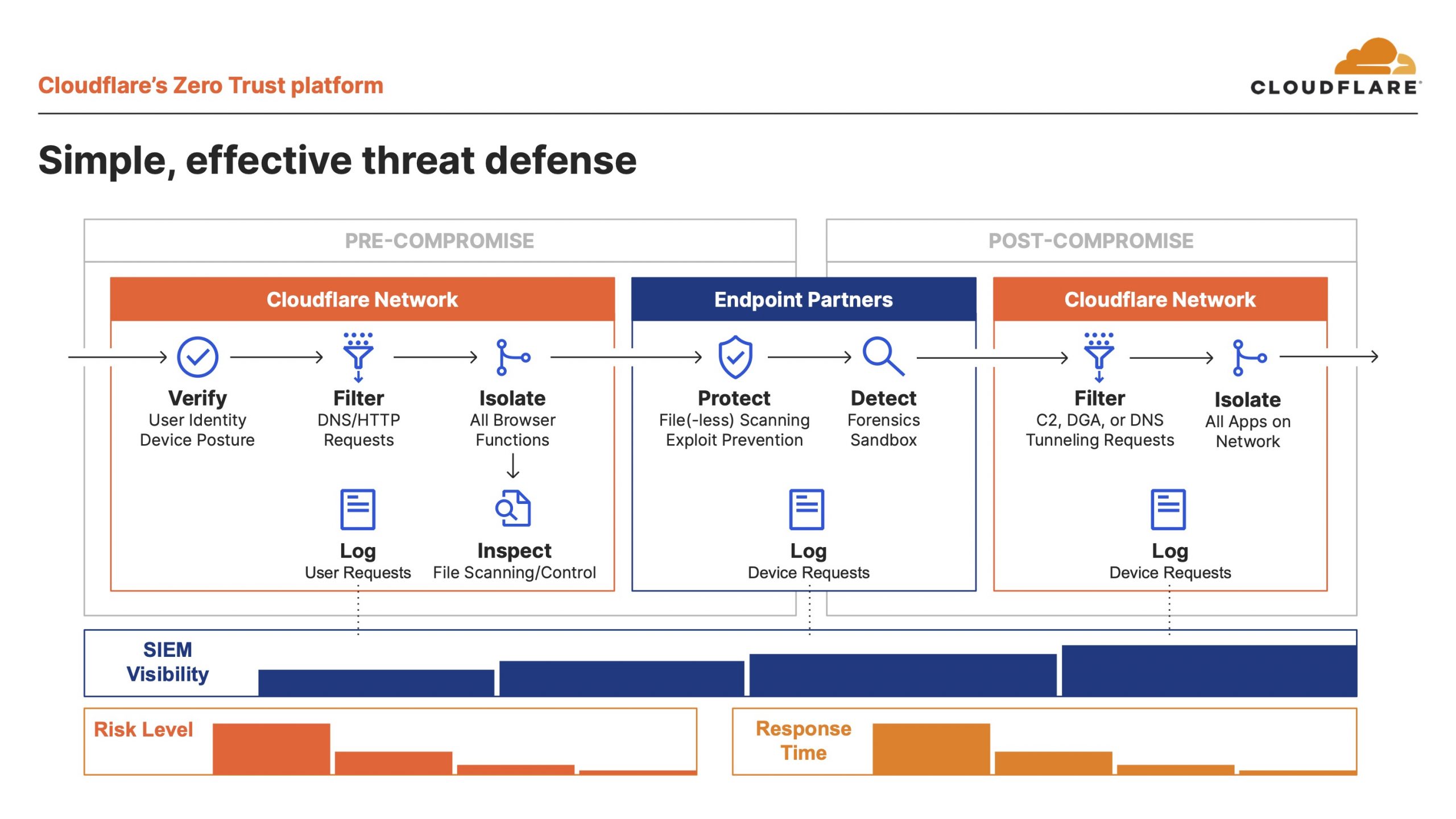
Cloudflare’s Zero Trust platform offers solutions for two problems. Traditionally, multiple point products require multiple policy managers and multiple client deployments. Cloudflare, however, offers one seamless platform that uses one policy manager and one client deployment. The other issue with traditional approaches is that platforms only integrate one identity provider (IdP) repeatedly and inconsistently. To address this, Cloudflare integrates many IdPs and tenants of the same IdP just once.
Concluding his presentation, Fernando emphasises the simple and effective threat defence that Cloudflare offers. In a fast-changing environment and changes in work models and culture, Cloudflare secures the networks of agencies working with a remote workforce seamlessly.
Starting a Zero Trust Government

Jeffrey Brown, Chief Information Security Officer, State of Connecticut spoke next on the establishment of a zero-trust government in his work in Connecticut.
The state of Connecticut has over 50 state agencies and three branches – executive, legislative and judicial. The key industries are financial services and insurance; aerospace and defence; bioscience and healthcare; film, TV and digital media; and advanced manufacturing.
In terms of management, the state government has the responsibility of handling a 24/7 Digital government, election infrastructure, 911 network, state critical infrastructure, healthcare, finance, transportation and the trust of 3.5 million citizens.
For Jeffery, the “chewy centre”, perimeter security model, whereby everyone inside the corporate network is trusted, is dead. Zero trust is now the dominant model of cybersecurity. The assumption with Zero Trust is that the network has already been compromised. It is an approach that deems networks both inside and outside as critical. There is a stricter identity verification process whereby every user and device has to prove that they are not a cyber attacker.
Jeffery believes that trust is a vulnerability that can be mitigated and that no one can achieve perfect trust. For him, “it is a balance.” He outlines three approaches that the state of Connecticut has undertaken:
- Know that all zero trust schools of thought make sense only if they support the business
- Learn about the most common frameworks (NIST 800-207)
- Understand that zero trust is a marathon, not a sprint. Not everyone can achieve zero trust, but everyone can adopt it.
In pursuing zero trust government, there were many lessons that Jeffery learnt along the way. In essence, it is a process with different components such as implementing multifactor authentication (MFA) everywhere, having 24/7/365 security monitoring, addressing identity and access management, leaning on federal partners and ultimately planning for the future.
Before closing his segment, he encourages delegates to take a risk-based approach to ensure that the most important pieces are first addressed and look at how Zero Trust can be implemented within their agencies to enable the government to do more.
Understanding the fundamentals of Zero Trust architecture

Gerald Caron: The nuts and bolts of Zero Trust architecture
Gerald Caron, Chief Information Officer & Assistant Inspector General for Information Technology U.S. Department of Health and Human Services, Office of the Inspector General, shared the various aspects and characteristics of Zero Trust architecture.
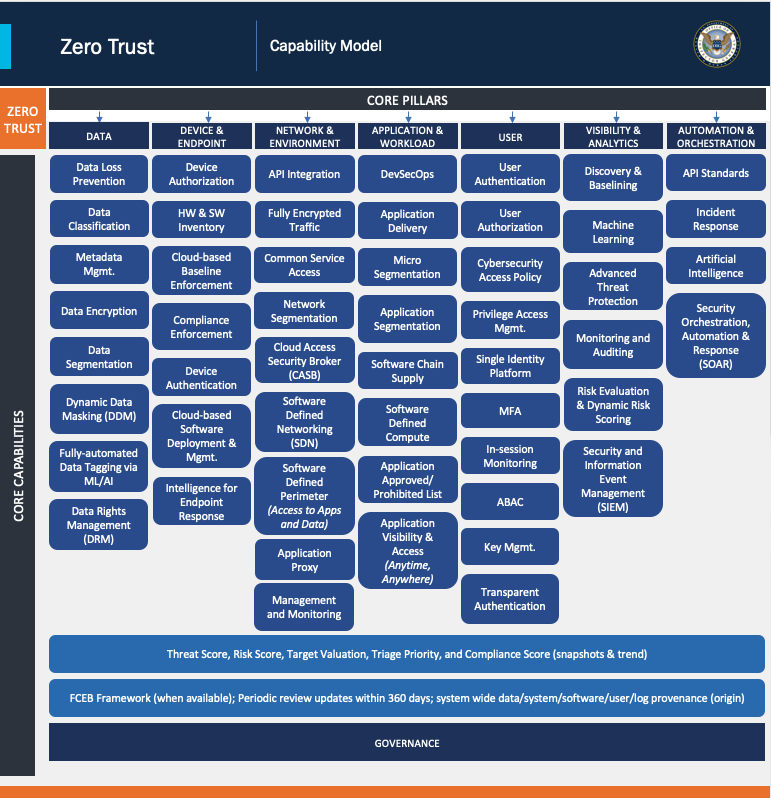
While most people focus on the identity aspect of Zero Trust, Gerald believes that it is the data that organisations are trying to protect – that is the goal of Zero Trust. Beginning with Zero Trust core principles, Gerald notes that Zero Trust hinges on five core principles related to trusting no one and having the protection of the right size.
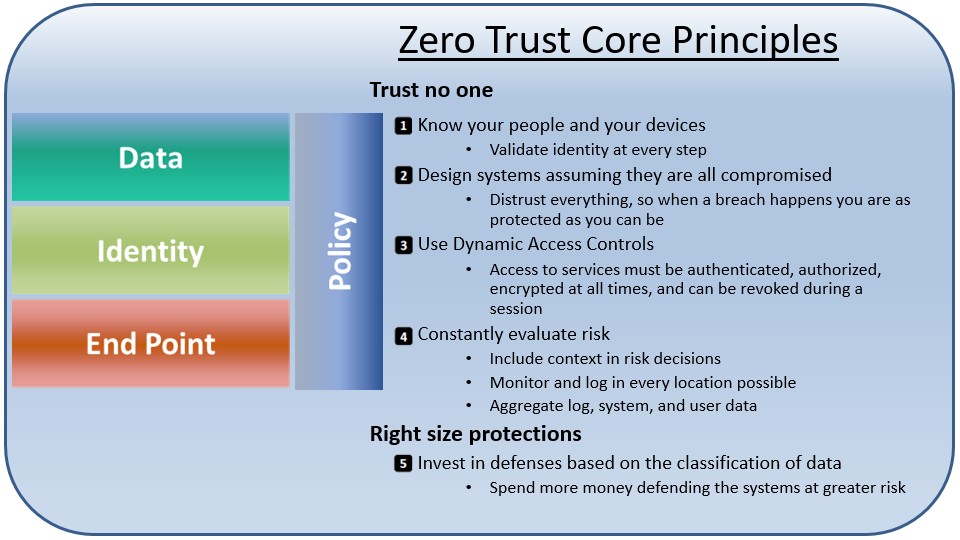
Trust no one
- Know your people and your devices: Validate identity at every step
- Design systems assuming they are all compromised: Distrust everything, so when a breach happens you are as protected as you can be
- Use Dynamic Access Controls: Access to services must be authenticated, authorised, encrypted at all times, and can be revoked during a session
- Constantly evaluate risk: Include context in risk decisions; Monitor and log in every location possible; Aggregate log, system, and user data
Right size protections
- Invest in defences based on the classification of data: Spend more money defending the systems at greater risk
Gerald adds that not all data is equally important. Organisations need to identify what is important. Zero Trust recognises these differences and categorises data based on its sensitivity and mission criticality. This categorisation is considered when protecting the data and granting access.
Apart from that, the paths are also not equal. In a Zero Trust environment, the path the data takes between the client and host impacts the level of risk, thus impacting how much a connection can be trusted. Connections with higher risk either restrict access to data/services or require a higher level of authentication.
While traditional authentication checks a user’s credentials once and uses that initial authentication for any subsequent activity before log-out, identity authentication is much stricter in Zero Trust. Multiple factors are considered when validating access, including the user’s role and location, the state of the device attempting access, and the data or services being accessed. Organisations need to look at all these factors to develop a risk-tolerance framework to decide what a user can or cannot do.
At the same time, Zero Trust assesses the state of each device attempting to access the network – for example, the device’s operating system version and patch level – to ensure that the client does not introduce additional risk to the environment.
Zero trust architecture features dynamic access control. While traditional authentication happens once, at the start of the session, and remains in place, Zero Trust authenticates dynamically each time new data is accessed or when something triggers a change in risk.
Gerald shares that a Step-up event in a Zero Trust environment can mitigate some of the potential risks a client may introduce. During the event, the system requires an additional authentication that can help control, although not entirely offset, the risk introduced by a client.
As for monitoring, continuous, detailed monitoring and logging are critical elements of Zero Trust as they contribute to a holistic picture of each user’s session and the overall environment. Data collected from monitoring and logging is linked with known threats and data/system sensitivity to drive cyber protections.
Gerald emphasises the importance of understanding the baseline and knowing what “normal” looks like – only then can organisations react to “abnormal.” As for risk evaluation in a Zero Trust environment, the authentication is evaluated dynamically, each time new data or resources are accessed or when something triggers a change in risk level.
Before ending his presentation, Gerald cautioned against being caught up with the tools and technology. He emphasises the importance of first understanding the organisation’s risk tolerance, methodology and threshold for risk. He also recommended his capability model as a way to understand the organisation’s functional capability and identify where the gaps are.
Gerald hopes that his presentation offered a quick overview of Zero Trust architecture that could help kick start the journey for delegates thinking about adopting a Zero Trust approach.
Interactive Discussion
After the informative presentations, delegates participated in interactive discussions facilitated by polling questions. This activity is designed to provide live-audience interaction, promote engagement, hear real-life experiences, and facilitate discussions that impart professional learning and development for participants.
A delegate asked the speakers about their experience of working within Zero Trust architectures. For him, the Zero Trust environment have caused people to be dispossessed of the services that they used to enjoy.
 In response to that, Gerald points out that “humans are the weakest point” and it is not always a malicious person but someone trying to get their job done. It is vital to understand how users work and what data is needed. He sees Zero Trust as an opportunity to improve operations. By looking into various technologies, the government is essentially optimising processes and performance enhancements. However, he stresses the importance of understanding the user in the process of implementing new systems and not limiting it to the IT domain.
In response to that, Gerald points out that “humans are the weakest point” and it is not always a malicious person but someone trying to get their job done. It is vital to understand how users work and what data is needed. He sees Zero Trust as an opportunity to improve operations. By looking into various technologies, the government is essentially optimising processes and performance enhancements. However, he stresses the importance of understanding the user in the process of implementing new systems and not limiting it to the IT domain.
Fernando adds that implementing frameworks with legacy technologies that it where there will be a negative user experience. The end goal is to make the user experience as seamless as possible. Therefore, addressing legacy technology will be important in this process.
Mohit is convinced that it is not only about legacy technology but also legacy governance and processes. Change and transformation have to be holistic, encompassing all aspects.
The first poll inquired how delegates plan to implement Zero Trust across their extended environment. Most (34%) indicated that they have already started implementing zero trust with a primary focus on identifying our critical assets, followed by delegates who are not yet ready to implement zero-trust due to the lack of resources and skills needed(19%). The rest of the delegates indicated that they work with multiple security partners to build a practical and pragmatic roadmap to implement zero-trust (14%) or have made huge investments in different technologies and are not sure where to start due to operational complexities (14%).
A delegate observed that the consideration for Zero Trust needs to be ground in yielding a particular business value. At the same time, the end-user friction needs to be considered – the processes need to be made less difficult for everyone in the company.
Fernando opines that the user experience needs to lubricate the process of building a Zero Trust architecture. The technology is there to allow people to move faster. Mohit felt that there was resistance when the cloud-first came out but governments are slowly changing their policy to embrace the cloud.
On their organisation’s current security priority, over half the delegates indicated that enabling Endpoint Mobile Management & Protection (EMM) / BYOD/ IAM is their highest priority (55%). The rest of the equally divided between employing DDoS, Web Application Firewall, Bot Management, Data Loss Prevention (15%), ensuring secure access to applications hosted on cloud service providers (e.g. Microsoft, Amazon, Google) (15%), and ‘others’ (15%)
In response to the results, Fernando observes that the emphasis on the end-point could be because of the hybrid situation that organisations are in.
Exploring key drivers for their organisation in initiating and augmenting an identity access / Zero Trust management programme, exactly half the delegates indicated security/data protection/ breach prevention was the key driver. That is followed by internal/industry/regulatory compliance (19%), response to audit or security incidents (13%). The rest of the votes were split evenly between operational efficiency (6%), reduce endpoint, insider and IoT security threats (6%) and others (6%).
On the best scenario that describes their organisation’s journey, nearly 3 out of 5 of the delegates are of the view that ZTNA solution will work alongside VPN serving different use cases for years to come (59%). Other delegates felt that they see shifting users gradually from a VPN to a ZTNA solution but will always keep VPN for a core set of users (29%). Just over a tenth (10%) acknowledged they would migrate all users to a ZTNA solution (12%).
Looking at the polls, Fernando opines that the reason why people might have a foot on each side in ZTNA and VPN is due to the focus on user and identity in the marketing of services. Gerald adds that it might have to do with culture and the resistance to change. He believes that VPN is not iron-clad and that he would rather be effective than compliant.

When asked about the Zero Trust tenets that are most compelling to their organisation, just under a third (30%) placed continuous authentication, authorisation/Trust earned through entity verification at the top. This was followed equally by end-to-end access visibility and audit (21%) and data protection, e.g. secure connection (21%). The rest of the delegates were compelled by the facilitation of least privileged access (14%), no trust distinction between an internal or external network (7%) and others (7%).
The final poll inquired on the most likely approach that the delegate’s organisation might take in evolution to SASE (Secure Access Service Edge). An overwhelming number of delegates are likely to take a best of breed approach to select partners that are most appropriate to my organisation’s needs (77%). The remaining delegates were split between staying with existing partners and consolidating as necessary (15%) and looking for partners who can provide a complete SASE solution (8%).
Conclusion
In closing, Mark Huang, Product Director, Securecraft, acknowledged the mounting challenges in a drastically changed world. He emphasised that the journey of setting up a Zero Trust architecture need not be taken alone – Cloudflare at Securecraft can help government agencies with the task of making their services more secure.
Before ending the session, Mark thanked the delegates for the robust discussions and invited delegates to reach out to him and the team if they wanted a deeper understanding of how to get started on securing the government.
As the local distributor of Cloudflare, Mark emphasised that Securecraft would be more than happy to offer any support that delegates might need in their digital transformation journey.