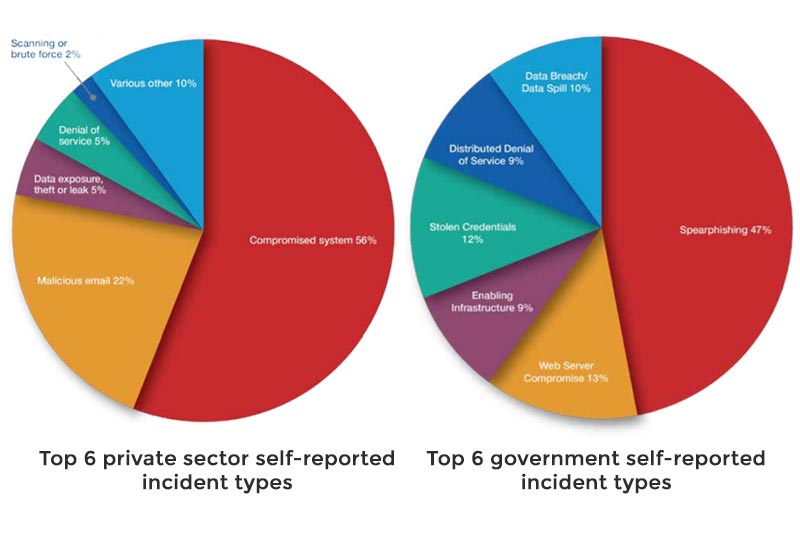
Above image taken from ACSC Threat Report 2017, page 20-21
The Australian Cyber Security Centre (ACSC) released its Threat Report 2017 today. The ACSC is the focal point for the cyber security efforts of the Australian Signals Directorate (ASD), Computer Emergency Response Team (CERT) Australia, the Defence Intelligence Organisation (DIO), the Australian Criminal Intelligence Commission (ACIC), the Australian Federal Police (AFP), and the Australian Security Intelligence Organisation (ASIO). ACSC works with government and business to reduce the security risk to Australia’s government networks, systems of national interest, and targets of cybercrime where there is a significant impact to security or prosperity.
The ACSC in the last 12 months has identified 47,000 cyber incidents, a 15 percent increase on last year. Over half of these incidents were online scams or fraud, which saw an increase of over 22 percent. In contrast, only one instance of cybercrime has fallen, the prevalence of illegal or prohibited material. This is down by 3.1 percent.
In 2016-17, the ACSC reported that 7,283 cyber security incidents affected major Australian businesses. The ACSC also responded to 734 cyber incidents affecting private sector systems of national interest and critical infrastructure providers. The ACSC has seen targeting of non-traditional victims, such as automotive, accommodation, and hospitality businesses increase by around 50 percent.
During the release of the report, the Hon Dan Tehan MP, the Minister for Veterans' Affairs, Minister for Defence Personnel and Minister Assisting the Prime Minister for Cyber Security, said, "If you are hit by cybercrime, don’t regret it, report it. If you don’t tell us you’ve been hit, we can’t help you. It’s hard enough to catch the criminals who did it. But if you don’t report it, it makes it impossible and leads to more victims." During 2016-17, of the reported incidents that impacted business, fewer than 60 percent came forward to report what had happened. For the other 40 percent, the incidents were identified by the ACSC.
In this report, ACSC has observed two distinct trends regarding the level of sophistication employed by adversaries and cybercriminals. At one end of the spectrum, increasingly sophisticated exploits are being developed and deployed against well-protected networks, particularly government networks. This reflects investment in new tools and techniques to keep pace with efforts to protect networks. On the other end, the ACSC continues to observe many adversaries, particularly criminals, compromising networks lacking baseline cyber security measures, using publicly known vulnerabilities that have known mitigations.
The report identifies the following as major current challenges:
Ransomware
Ransomware continues to grow as a method of extorting funds from a wide range of victims. The report notes some adversaries have expanded their operations to a pseudo-franchise model, dubbed ransomware-as-a-service (RaaS).
RaaS provides entry to the ransomware market for anyone willing to pay, regardless of technical capability. RaaS developers write ransomware, build the infrastructure required to run a campaign and sell it through darknet markets. The infrastructure is generally sold at a low price, with a percentage of profits returned to the vendor. Purchasers (known as affiliates) are generally provided access to a darknet-based dashboard. The dashboard provides a range of capabilities, usually including ransomware customisation, as well as tracking of successful infections and ransoms paid.
The most commonly reported ransomware delivery method is mass-market untargeted phishing campaigns. Large-scale, untargeted phishing campaigns are generally cheap and relatively simple to run. A fully-patched and protected device can be infected through phishing by the victim downloading a malicious attachment. The second most common form of delivery is through an exploit kit, a software tool kit, which runs on a web service and contains a variety of known exploits to infect visitors to a website with malware. This does not requiring a person to download a file – simply visiting a compromised website while running vulnerable software is sufficient.
Credential-harvesting malware
According to the report, this poses an increasing threat to Australian networks, in particular to the financial sector, by stealing credentials, such as login details. The ACSC has observed a shift in cybercriminal’s targeting activities and capabilities, specifically the development of expertise and malware to target Australia and Android smartphones. Credential-harvesting malware designed for smartphones will likely increase due to the amount of information stored on these devices, and their increased use for activities such as online banking and purchases. Similarly, ransomware which targets smartphones will likely increase in the future as people store personal information such as photos and contacts on these devices.
Social engineering
As Australian network defences become more resistant to cyber intrusion, increasingly sophisticated social engineering provides a way to bypass security protocols.
This ranges from broad phishing emails, through to targeted phishing emails, to individually tailored communications. Some of the most sophisticated social engineering involves simultaneous approaches through different communications platforms, including phone calls.
The ACSC has also identified cybercriminals using compromised accounts of networks known to their target in order to support their campaigns. Social media provides ideal platforms for cybercriminals to obtain personal information to target victims. Malicious adversaries are able to research businesses, use false social media accounts, and compromise legitimate accounts, enabling them to impersonate business and government officials.
The use of social engineering is particularly prominent in business email compromise (BEC). Over 2016-17, reports to the ACIC’s Australian Cybercrime Online Reporting Network (ACORN) indicated losses of over AU$20 million due to business email compromise (BEC), up from AU$8.6 million in 2015-16. BEC can take many forms but most commonly involves impersonating a senior employee to change invoice details or generate a sense of urgency to bypass anti-fraud processes. Many cases of BEC schemes rely solely on social engineering techniques and spoofed email addresses, but some also use malware to access computer systems and company information.
Threats associated with outsourcing and supply chain
Third parties, that is vendors that provide services to a company or agency are being increasingly targeted. Companies that provide products or services through outsourcing usually have trusted relationships with their customers and are provided with extensive access.
A malicious adversary could target a provider’s customer through methods including exploiting the direct connectivity that a provider has with customer data and networks or modifying the provider's software or other products with malicious content, which is then installed on customer networks or gaining access to credentials to allow seemingly legitimate access to the target network.
Personally identifiable information (PII)
Cybercriminals continued to seek access to repositories of large amounts of PII to facilitate financial crimes and identity theft. Government and commercial bulk data repositories provide a single point of stora
ge for valuable information on large numbers of Australians.
Basic information, such as name, birth date and address, is often enough for criminals to impersonate victims. Cybercriminals may also try to extort money from organisations and individuals by threatening to release PII. Terrorists and hacktivists have publicly disclosed PII in order to embarrass, intimidate or threaten individuals, government and commercial organisations in ‘hack and release’ operations.
Malicious use of leaked tools
The public release of computer network exploitation (CNE) tools by groups such as the Shadow Brokers will improve the capabilities of malicious cyber adversaries. Less capable adversaries are likely to adopt these tools and use them on systems that remain vulnerable due to ineffective patching or updating. More capable adversaries may incorporate the tools and knowledge gained into their existing malware development efforts.
Attackers have demonstrated the ability to quickly use zero-day vulnerabilities – vulnerabilities in software unknown to the vendor. The ACSC has seen cyber adversaries modify them to be effective against current systems and circumvent some of the available patches.
Implementing timely patching and system-hardening regimes, and upgrading unsupported operating systems will mitigate most of the risk.
Router scanning
Throughout 2017, the ACSC and its international partners continued to observe the targeting of routers, including Australian routers, by malicious, sophisticated threat adversaries. This invovles automated scanning to identify vulnerable routers, and the subsequent extraction of configuration files. A configuration file stores various settings, including security settings and passwords. Accessing a router’s configuration file may ultimately allow a malicious adversary to modify the router settings, enabling control of internet communications on that device.
Internet of Things (IoT)
Security in IoT devices, such as smartphones and tablets, is not always a top priority during their creation. They are created for automation and to improve efficiency. Their increased integration into the ecosystem introduces significant security risks.
A lack of standardisation and the absence of any agreed security baseline means the proliferation of these devices is introducing potential for significant security risks. Additionally, connecting devices that can change the real-world environment (such as medical devices, cars, airconditioners, fridges and door locks) through the manipulation of an online service also increases the potential impact of a compromise.
Distributed Denial of Service threats
According to the report, Distributed Denial of Service activity will remain a threat to internet-connected systems for the foreseeable future. The means and mechanisms may change, but it will remain an enduring threat with demonstrated utility for state, criminal and issue motivated groups. Australian systems may be affected by DDoS activity occurring outside Australia as DDoS threats not only affect a given website or service, but can also affect related systems through interdependencies.